This topic provides an overview of the key concepts and terminology you should be familiar with before implementing authentication in your applications.
Security in ArcGIS
ArcGIS is a secure system that requires authentication to access all secure apps, content, data, and services. It implements industry-standard protocols to ensure that only authorized users and applications can access secure resources.
Some common workflows that use security in ArcGIS are:
- ArcGIS users sign in to apps such as ArcGIS Pro, Map Viewer and Scene Viewer.
- Developers create custom applications that use authentication to access secure resources.
- Administrators manage the privileges and roles of users to enhance security within their organization.
- Members of an organization upload and share content securely in a portal.
What is authentication?
Authentication is the process of verifying the identity of a user or application in ArcGIS. Authentication allows users and applications to access secure resources such as a portal, location services, and other services.
Authorization is the process of verifying client privileges prior to accessing a secure resource. After users and applications successfully authenticate with ArcGIS, the service they are trying to access will authorize the request if they have the appropriate privileges.
How authentication works
ArcGIS uses token-based authentication for all requests. Authentication works by interacting with a portal service to get an access token. The access token contains information that determines the privileges of the application as well as the associated ArcGIS account. Once obtained, the access token is included in requests to provide authorization for secure resources.
The general process of authentication includes the following:
- Authenticate with a portal to get an access token.
- Use the access token to authorize requests to secure resources.
Below is a sample HTTP request to access a secure resource in ArcGIS with an access token.
https://<SERVICE_URL>?token=<YOUR_ACCESS_TOKEN>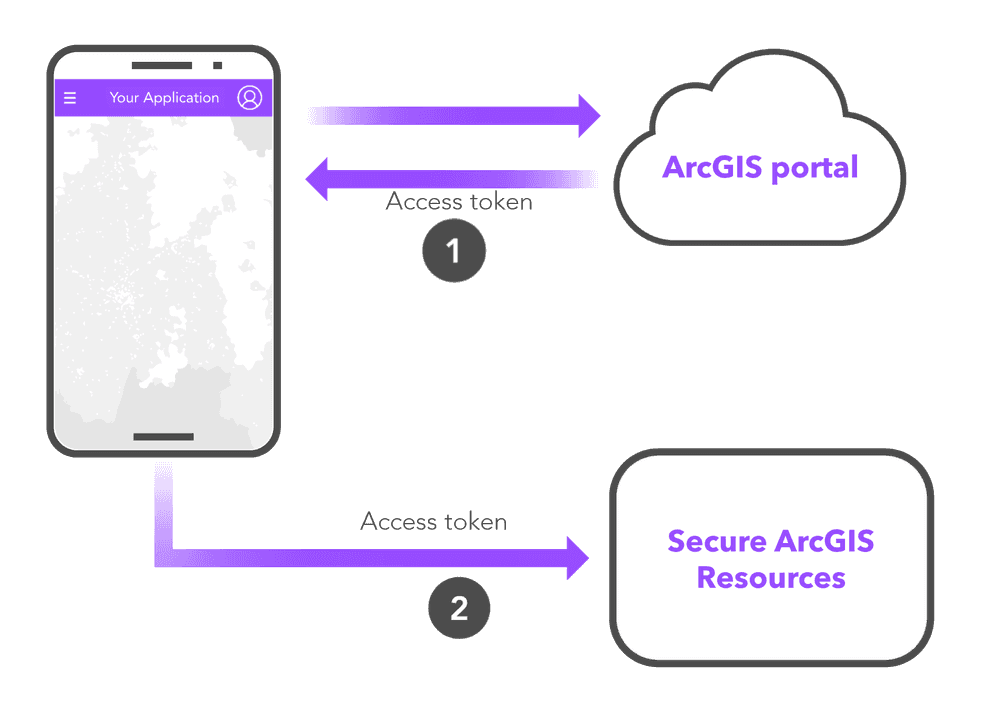
Types of authentication
ArcGIS supports three types of authentication to get an access token. Each type requires following a specific workflow and supports the development of a specific type of application.
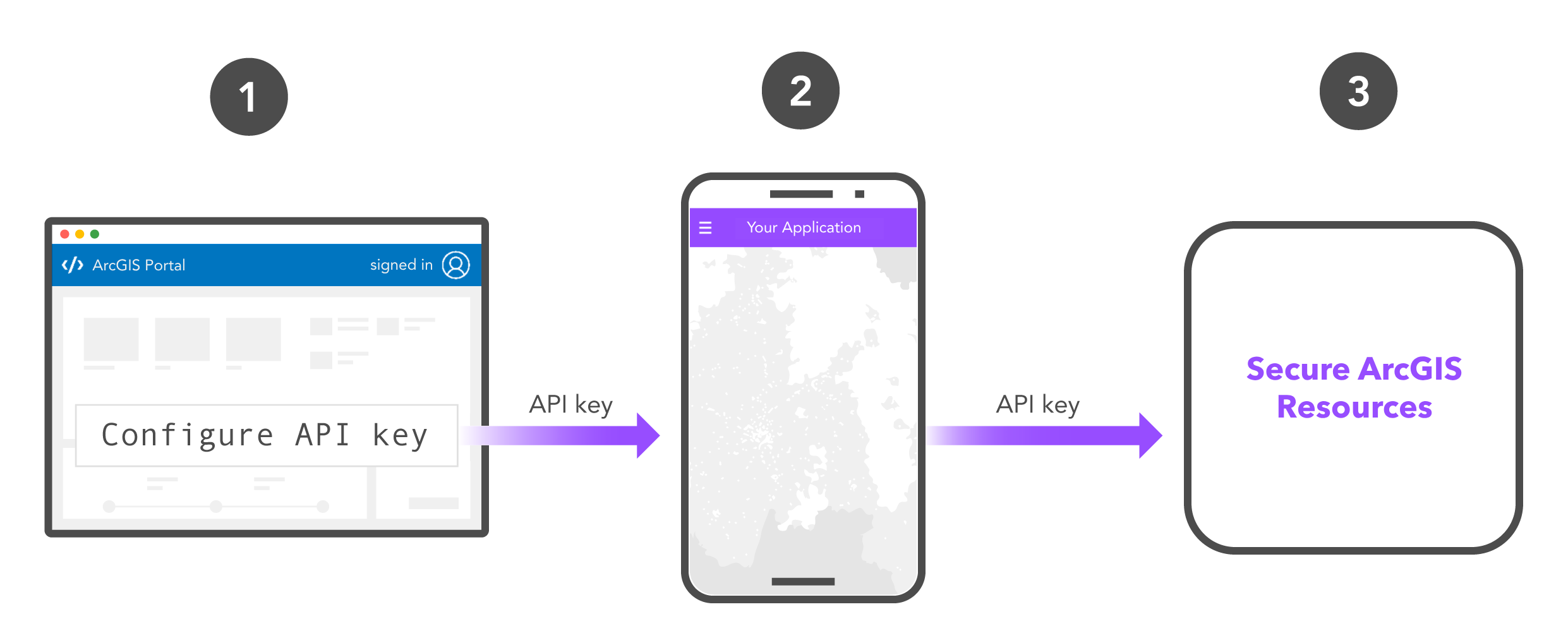
API key authentication
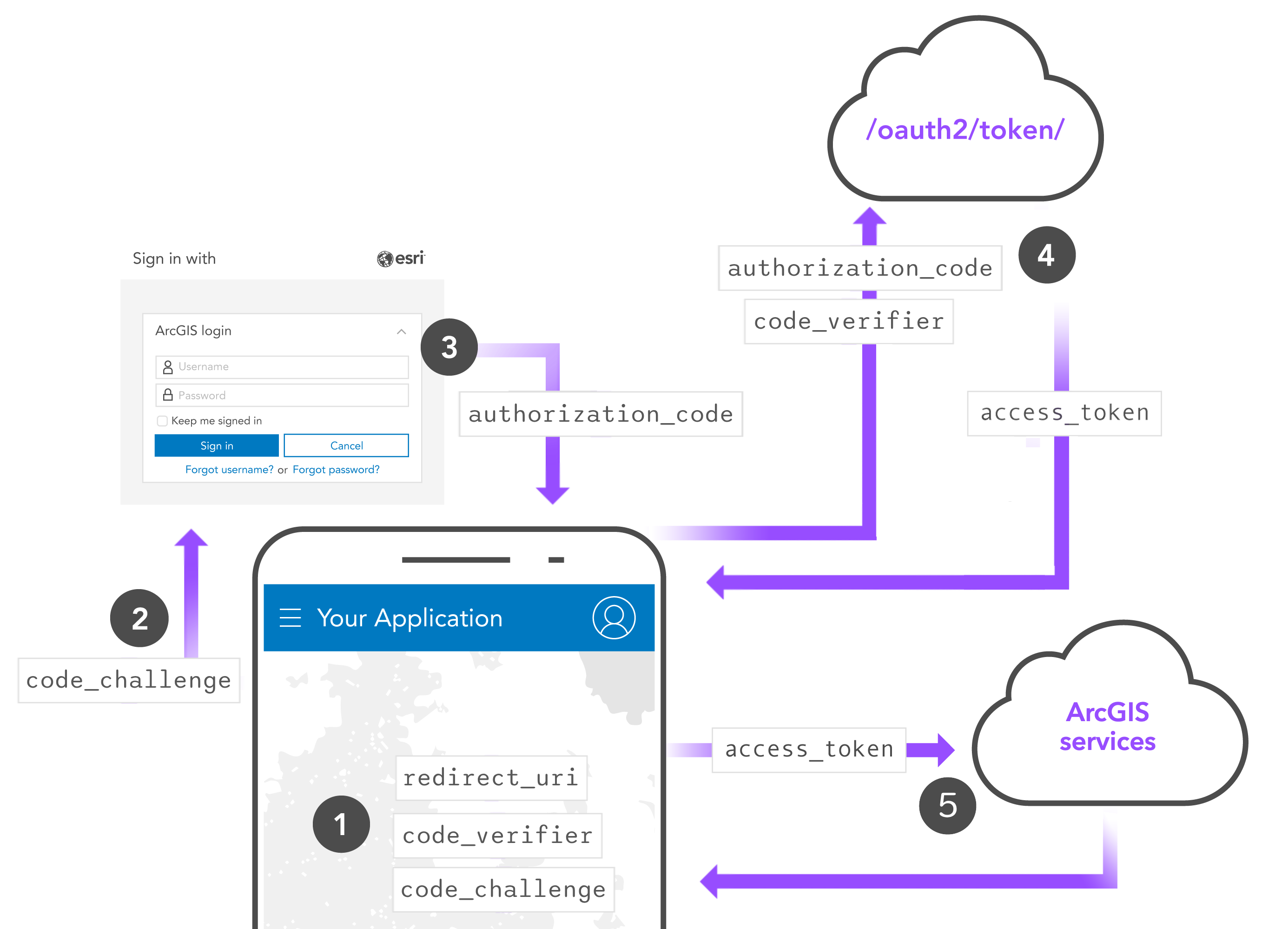
User authentication
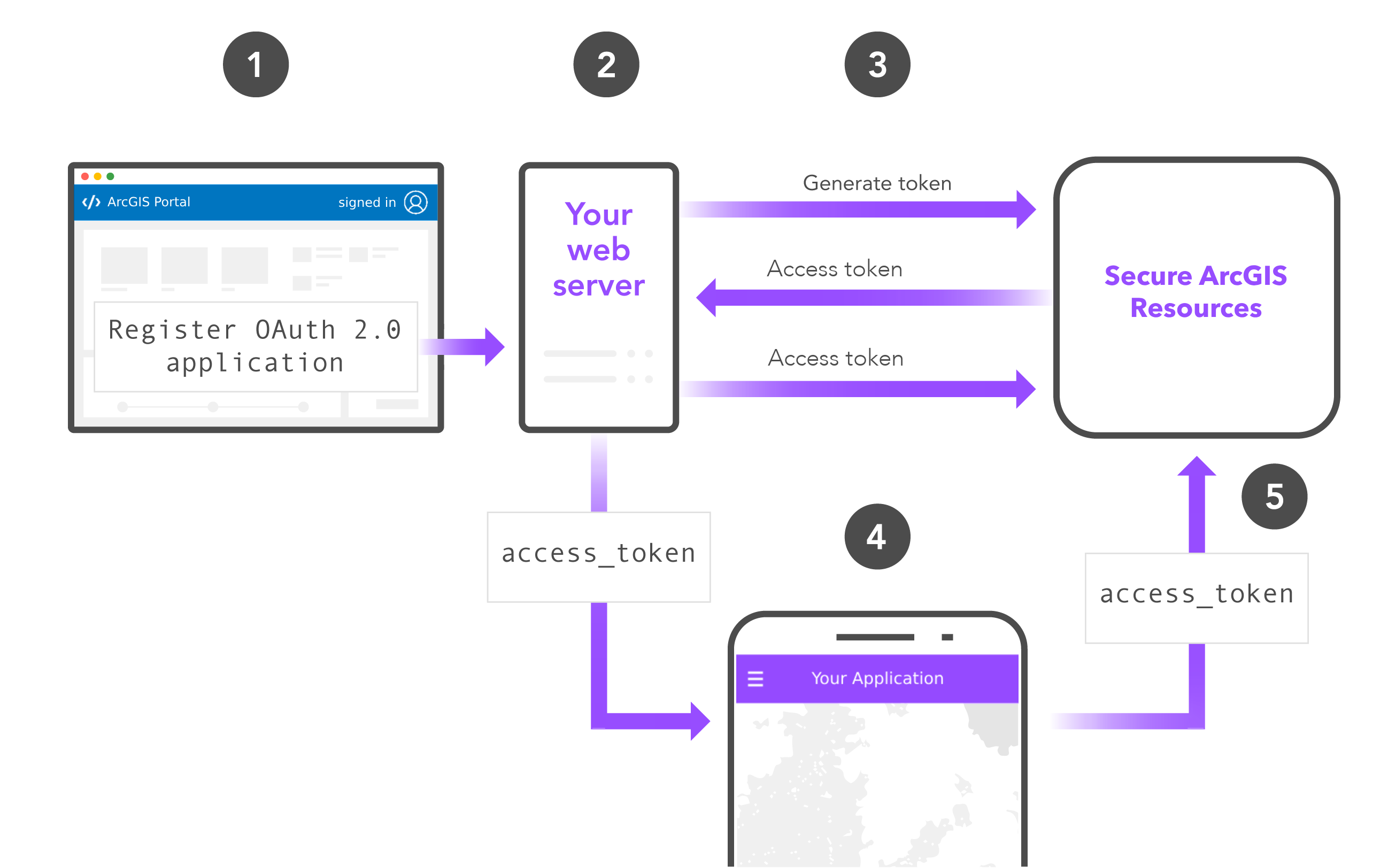
App authentication
Authentication comparison
The following table provides an overview of the functionality available with each type of authentication:
| API key authentication | User authentication | App authentication | |
|---|---|---|---|
| ArcGIS Location Services | |||
| Data services (Item access) | |||
| Spatial analysis services | 1 | 1 | |
| Portal service (General privileges) | 1 | 1 | |
| Portal service (Admin privileges) | 1 | 1 |
- 1. Supported with ArcGIS Online and ArcGIS Location Platform.
Terminology
This section contains important terminology you should be familiar with before implementing authentication in your apps.
ArcGIS accounts
You need an ArcGIS account to implement authentication in custom applications. The following table shows the supported types of authentication for each type of account:
| ArcGIS Location Platform account | ArcGIS Online account | ArcGIS Enterprise account | |
|---|---|---|---|
| API key authentication | 1 | 2 | |
| User authentication | |||
| App authentication | 1 | 2 |
- 1. Requires an administrator account or a custom role with developer privileges.
- 2. Supported in ArcGIS Enterprise 11.4 or greater. Requires an administrator account or a custom role with developer privileges.
If you are using an ArcGIS Online or an ArcGIS Enterprise account, your account must have certain privileges enabled to create developer credentials with privileges and item access. To learn more, go to the FAQ.
Public applications
A public application is an application developers create that does not require users to sign in with an ArcGIS account.
Public applications typically implement API key authentication or app authentication to authenticate requests to secure resources without prompting users to sign in. Usage costs for accessing secure resources in a public application are billed to the developer's account. Developers with an ArcGIS Online or ArcGIS Enterprise account can choose to omit authentication in public apps if the application only accesses resources with a sharing level set to Everyone (public).
Private applications
A private application is an application developers create that requires users to sign in with an ArcGIS account. Private applications implement user authentication and are typically built by ArcGIS Online or Enterprise developers for members of an organization. Usage costs for accessing secure resources in a private application are billed to the accounts of users.
Developer credentials
Developer credentials are a type of item in a portal that contains the necessary properties for authentication. You can create and manage developer credentials in your portal to support all types of authentication. In most cases, a developer credential is created for every application you create.
You can use developer credentials to:
- Create, regenerate, and invalidate API keys in API key authentication.
- Obtain an OAuth 2.0 client ID for user authentication.
- Obtain an OAuth 2.0 client ID and client secret for app authentication.
- Define the privileges and item access of your application.
- Authorize redirect URIs and referrer domains to improve application security.
Privileges
A privilege is a set of permissions that grant access to secure resources and functionality in ArcGIS. You use privileges to define the capabilities of a user account or developer credentials for a custom application.
Privileges can be applied to ArcGIS accounts and developer credentials:
- Privileges for users: Privileges define the capabilities and permissions for users in an organization. They are determined by the user type and role assigned to the account.
- Privileges for developer credentials: Privileges defined for developer credentials for custom applications you are building. They determine the capabilities and permissions of the access tokens used by your applications.
Access tokens
An access token is an authorization string that provides access to secure ArcGIS resources. It can be used to access resources such as ArcGIS services or items in a portal. To get an access token, you need to implement a type of authentication. The access token's capabilities are determined by the privileges associated with it.
Example of an access token:
AAPTKUgfudpnh_cXrZ7wRiqGE4q0VCQENKpafTPqVh27cldNPiqORWEyVueCmI67s3ebSNEYl0Sn3IitIyf18X8PxF3N8m9ZE30i5iwGHtGfnv6-DoKA-C8-lJ9GM30s-Wxn75jLBdnQnMjIgwVXEjIoualIMSfk4IWraDv3GMV8XP3fAUA73P23Vfs-THx2QjfDNVD3iuGCqLG0udK_TVLchskcBFVbsj1PRWXGcFaKKzdPkwWMXps_4P_cZEBAZdImAT1_L1aY2CIyPortal
An ArcGIS portal is a website with applications, tools, and functionality for creating and sharing geospatial content and data. A portal plays a key role in supporting authentication. It has built in security functionality to control access to sensitive data, manage users, and protect your organization. It also provides important tools for developers that allow them to create developer credentials required to build custom applications.
The portal supports the following security features:
- Membership: Only members can sign in, view content, access applications and tools, and participate in the organization/portal.
- Item sharing levels: Item sharing levels can be private, group, organization, or public. Only users with the correct privileges can access items in a portal.
- Groups: Members can create groups to share items with specific members.
- Roles: Administrators can grant custom roles to a member with privileges that specify that items, tools, and applications the member is allowed to access.
Additionally, a portal's underlying portal service is responsible for granting access tokens for Authentication.
Secure resources
The following resources are secure and require authentication to access:
-
Portal: A portal is secure and requires users and applications to sign in. The underlying portal service is also secure and requires authentication to access.
-
Secure items: All content items in a portal are secure and may require authentication depending on their sharing level. Items can also be shared with specific groups in an organization.
-
ArcGIS services: All ArcGIS services hosted in Esri's infrastructure are secure, including location services, spatial analysis services, data services, and the portal service.
-
ArcGIS Enterprise services: All ArcGIS Enterprise services hosted in your own infrastructure are secure.
-
Low/No-code applications: Applications built using low/no-code builders are hosted in a portal and secure and may require authentication depending on their sharing level.
-
ArcGIS tools: All ArcGIS tools are secure, such as ArcGIS Pro, Map Viewer, Scene Viewer.
-
Subscriber and premium content: Subscriber content is a type of secure item hosted in ArcGIS Living Atlas that requires an ArcGIS Online account. Premium content is a subtype of subscriber content that consumes credits.
Tutorials
Create an API key
Create OAuth credentials for user authentication
Create OAuth credentials for app authentication
API support
- 1. Supported via ArcGIS REST JS